17+ Svg file xss ideas
Home » free svg idea » 17+ Svg file xss ideasYour Svg file xss images are available in this site. Svg file xss are a topic that is being searched for and liked by netizens today. You can Get the Svg file xss files here. Find and Download all free vectors.
If you’re searching for svg file xss pictures information related to the svg file xss interest, you have come to the ideal blog. Our website frequently gives you hints for seeing the highest quality video and picture content, please kindly surf and find more enlightening video articles and images that fit your interests.
Svg File Xss. XSS-Payload-List or Cross-Site Scripting XSS attacks are a type of injection in which malicious scripts are injected into otherwise benign and trusted web sites. PDF About Dangerous SVG. The fact that you can execute JavaScript from inside an image file presents an unexpected vector for XSS attacks. If a website loads a SVG file with an XSS payload it will get executed.
 Do You Allow To Load Svg Files You Have Xss Research Securitum Com From research.securitum.com
Do You Allow To Load Svg Files You Have Xss Research Securitum Com From research.securitum.com
Attacker can inject JS code into the svg file and due to the insecure handling of crafted svg file attacker can perform XSS attack. Corrupt SVG File With XSS. A collection of ways to defend against Cross-Site Scripting attacks ran through SVG files. This means that if they happen to save the SVG file and then view it any malicious JavaScript will still be executed on their device since on most devices the only software that can view SVGs are browsers. Here is a simple example of a 50x50 pixel green triangle. Yes XSS threats do exists when using SVG most browsers will not allow the script to run but if it is sent via email then it could potentially run.
Some links to issues.
Now a SVG file can be used in a XSS attack only by leveraging the. Place the cursor before the character and click Add twice to create a payload position. Xss through svg file. This way we may shrink the initial XSS attack vector as below. An img tag will not work. In addition to that in contact page users can upload svg files via file upload functionality.
 Source: brutelogic.com.br
Source: brutelogic.com.br
This means that if they happen to save the SVG file and then view it any malicious JavaScript will still be executed on their device since on most devices the only software that can view SVGs are browsers. Stored XSS also known as Persistent XSS is achieved when the server actually stores persists the malicious JavaScript payload. The SET_LANGUAGE parameter is affected by reflected XSS vulnerability. The value of the search term should now be. This is especially true for the first point in ThosTL67s answer.
 Source: brutelogic.com.br
Source: brutelogic.com.br
Href xss attributeName href keyTimes 001 values httpisecpljavascriptalert 1X a id xss text x 20 y 20 XSS. The value of the search term should now be. Which when loaded will trigger the XSS payload marked above. Some links to issues. In Burp Intruder in the Payloads tab click Clear to.
 Source: youtube.com
Source: youtube.com
Any SVG file can contain javascript code but to execute it you have to be able to access the file directly via either writing it to the page or visiting the SVG file directly. Stored XSS also known as Persistent XSS is achieved when the server actually stores persists the malicious JavaScript payload. Href xss attributeName href keyTimes 001 values httpisecpljavascriptalert 1X a id xss text x 20 y 20 XSS. Corrupt SVG File With XSS. Any SVG file can contain javascript code but to execute it you have to be able to access the file directly via either writing it to the page or visiting the SVG file directly.
 Source: brutelogic.com.br
Source: brutelogic.com.br
Any SVG file can contain javascript code but to execute it you have to be able to access the file directly via either writing it to the page or visiting the SVG file directly. Stored XSS also known as Persistent XSS is achieved when the server actually stores persists the malicious JavaScript payload. Svg animate xlink. Now a SVG file can be used in a XSS attack only by leveraging the. A less common attack vector would be to embed JavaScript within an SVG image.
 Source: medium.com
Source: medium.com
XSS attacks can be carried out using SVGs. Protecting against XSS in SVG. Place the cursor before the character and click Add twice to create a payload position. An img tag will not work. As Result this allow an attacker to steal user session takeover user account make redirect user to.

This allows the image to scale flawlessly no matter the size or resolution. Enterprise Level CMS - Free and OpenSource - Community Driven - Secure. XSS attacks can be carried out using SVGs. A properly handled SVG file has become a gateway to the Persistent XSS attack. This is because any malicious JS within the SVG is still sent to the viewer.
 Source: medium.com
Source: medium.com
The value of the search term should now be. SVG stands for scalable vector graphics and instead of recording color and pixel placement such as a Bitmap or JPEG file type SVG images are created through mathematical formulas. Protecting against XSS in SVG. Stored XSS from file upload svg html Plone. Scalable Vector Graphics SVGs.
 Source: research.securitum.com
Source: research.securitum.com
XSS attacks can be carried out using SVGs. Href xss attributeName href keyTimes 001 values httpisecpljavascriptalert 1X a id xss text x 20 y 20 XSS. Enterprise Level CMS - Free and OpenSource - Community Driven - Secure. Here is a simple example of a 50x50 pixel green triangle. A working copy of these files is hosted on the site SVG XSS Defence Scenarios.
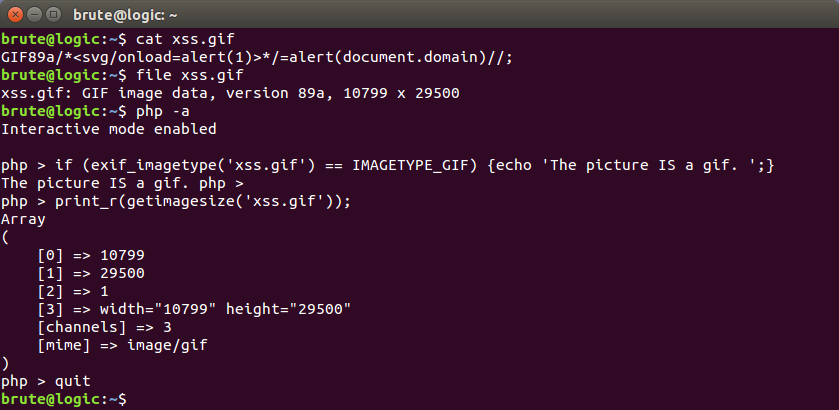 Source: brutelogic.com.br
Source: brutelogic.com.br
You just got stored XSS via a SVG file. Embedding it in eg. If a website loads a SVG file with an XSS payload it will get executed. Href xss attributeName href keyTimes 001 values httpisecpljavascriptalert 1X a id xss text x 20 y 20 XSS. A working copy of these files is hosted on the site SVG XSS Defence Scenarios.
 Source: research.securitum.com
Source: research.securitum.com
SVG Fun Time - Firefox SVG Vector Bypassing Chrome XSS Auditor. Visit the XSS cheat sheet and click Copy events to clipboard. A properly handled SVG file has become a gateway to the Persistent XSS attack. Which when loaded will trigger the XSS payload marked above. Protecting against XSS in SVG.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site convienient, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title svg file xss by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.